Security isn’t an afterthought - it’s a fundamental requirement for any production API. This post covers the OWASP API Security Top 10 vulnerabilities and practical Go implementations to protect your applications.
Authorization Patterns: RBAC and ABAC in Go
After authentication confirms user identity, authorization determines what they can access. This post covers two powerful authorization models: Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC), with practical Go implementations.
JWT Authentication in Go
Authentication verifies who users are, while authorization determines what they can access. This post covers implementing JWT (JSON Web Token) authentication in Go - the most common approach for stateless API authentication.
Kerberos on Hadoop

The Kerberos is an authentication protocol which creates tickets to allow communication between nodes on non-secured network. Ticket must be periodically triggered by kinit command by each user. In Kerberos we call users as principals. We can divided principals basically into several groups:
- System users – principals for communication between services in Hadoop cluster
- Common users
Setup LDAP for Apache Nifi
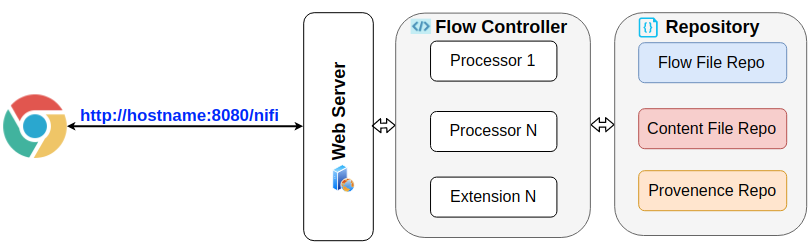
Default Apache Nifi installation comes without security layer which exposes the development UI. As a result, users can freely access the Nifi project development with knowledge about the hostname and binding Port. You can see two potential security risks:
- Flow controller attack : full policies to modify the processor on Flow Controller.
- API attack: external invoked requests to start/stop/delete Nifi components.